Sunday, May 14th, 2017
WannaCry/Wcry: How To Defend Against It

A ransomware worm called “WannaCry” has infected more than 100,000 computer systems in 104 countries since Friday, with Russia, Ukraine, and Taiwan being the top targets and the attack is still ongoing. Along with our peers in the industry, Smarttech’s Threat Research Team has been actively analysing the malware and its threats. The WannaCry ransomware needs to be a wake up call for everyone with weak security posture.
EternalBlue
The vulnerability used in this attack (code named EternalBlue) was among those leaked by the Shadow Brokers group that was allegedly stolen from the National Security Agency (NSA). The vulnerability was exploited to drop a file on the vulnerable system which would then be executed as a service. This would then drop the actual ransomware file onto the affected system, encrypting files with the .WNCRY extension.
This exploit was patched by Microsoft on March 14, however many organisations have not patched. It’s important to understand that while unpatched Windows computers exposing their SMB services can be remotely attacked with the “EternalBlue” exploit and infected by the WannaCry ransomware, the lack of existence of this vulnerability doesn’t really prevent the ransomware component from working. Nevertheless, the presence of this vulnerability appears to be the most significant factor that caused the outbreak. Microsoft also has released the patch for EOL systems (Windows XP and 2003 servers) – many of affected hosts use these OSes.
How it Works
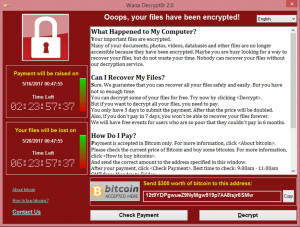
It is important to note that the virus is easily spreadable among all vulnerable computers on internal network and also tries to affect external networks. This may be just the beginning of a bigger campaign – the virus can be easy rewritten to use different vulnerability. There were already 2 versions of the virus released to the network. The first version had a so called “kill switch” to stop the virus from executing. Because security researchers have discovered this and stopped the first version very quickly the second version didn’t have such a solution. This “kill switch” is typical in virus prototypes which means hackers are still working on the code.
Recommendations
- Make sure that all hosts are running and have enabled endpoint security solutions
- Install the official patch (MS17-010) from Microsoft, which closes the affected SMB Server vulnerability used in this attack
- Disable the SMB protocol on systems that do not require it. Running unneeded services gives more ways for an attacker to find an exploitable vulnerability
- Deploy firewalls and detection and intrusion prevention systems. Configure firewalls to block access to known malicious IP addresses
- Conduct penetration tests and vulnerability assessments
- A properly tuned SIEM solution helps detect ransomware. It provides a holistic network overview and automated analysis of security events based on professionally configured parameters
- Last but not least, back up your files regularly
Finally, if you find yourself or your organisation infected, our Smarttech Incident Response team is happy to help you.
Contact Us
The data you supply here will not be added to any mailing list or given to any third party providers without further consent. View our Privacy Policy for more information.