Tuesday, June 27th, 2017
Ransomware Attacks Affecting Europe

Ransomware attacks have impacted businesses throughout Europe, in an infection reminiscent of last month’s WannaCry attack. The most severe damage is being reported by Ukrainian businesses. Systems have been compromised at Ukraine’s central bank, state telecom, municipal metro, and Kiev’s Boryspil Airport. Systems were also compromised at Ukraine’s Ukrenego electricity supplier, although a spokesperson said the power supply was unaffected by the ransomware attacks.
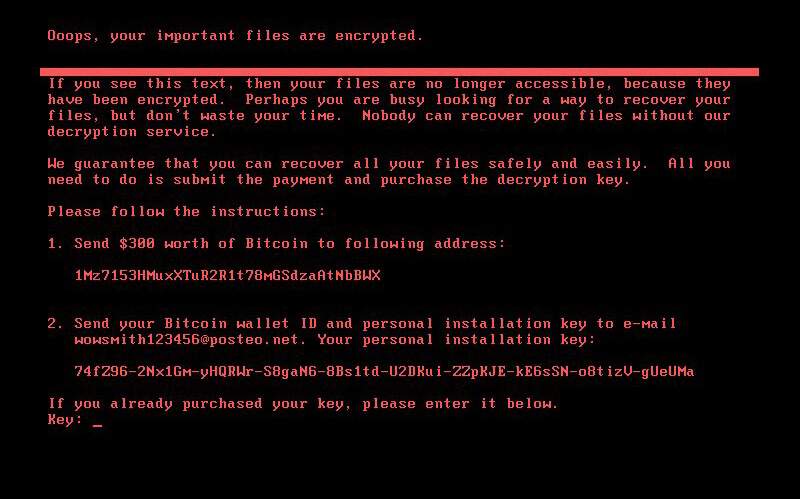
The ransomware attack has affected operations at the Chernobyl nuclear power plant too. It caused it to switch to manual radiation monitoring. Infections have also been reported in more isolated devices like point-of-sale terminals and ATMs.
The ransomware was a variant of the Petya/Mischa/GoldenEye ransomware. It seemed to be using both the ETERNALBLUE networking exploit developed by the NSA (and used by WannaCry) and a Microsoft Office/WordPad flaw discovered earlier this year.
We advise all businesses and organisations to patch immediately the following vulnerabilities. CVE-2017-0176, CVE-2017-0222, CVE-2017-0267 – CVE-2017-0280, CVE-2017-7269, CVE-2017-8461, CVE-2017-8464, CVE-2017-8487, CVE-2017-8543, CVE-2017-8552. Also, disable WMIC to stop lateral movement in your network.
Additionally, don’t wait and update your SMB protocol before it’s too late. If you are running Windows 8 or Windows Server 2012, you can use the Set-SMBServerConfiguration in a PowerShell command session. This allows you to enable or disable the SMBv1, SMBv2 and SMBv3 protocols on the server component with a few keywords. However, the process is a bit more involved if you are using older Windows versions, and you might need to edit specific registry keys.
Contact Us
The data you supply here will not be added to any mailing list or given to any third party providers without further consent. View our Privacy Policy for more information.