Friday, April 13th, 2018
Computer Vulnerabilities: How Safe Are Your Systems?

The first quarter of 2018 has recently just ended with a high number of critical vulnerabilities being discovered so far, from the early vibes of Spectre and Meltdown to Intel’s kernel leaking vulnerability up to the very recent Cisco smart install vulnerability. Towards the end of last year, we discussed a few major attacks that shock 2017 and we also predicted what the climate of cybersecurity will look like this year. In this post, we will be discussing what vulnerabilities are and a few major vulnerabilities that were exploited in 2017.
In very generic terms, computer vulnerability is a weakness that can be exploited by unauthorised users to carry out unauthorised actions on a computer system. It can be described as a flaw in the system that leaves it open to an attack. Most external attackers, for example, often look for vulnerability that can be exploited on a computer system while trying to gain access, steal information or any other unauthorised and malicious intentions they might have.
Let’s take a quick look at the recently discovered Cisco Smart Install vulnerability (CVE 2018-0171) for example. The vulnerability was due to the improper validation of packet data. An attacker could exploit this by sending a crafted Smart Install message to the affected device on port 4786. This exploit could allow the attacker cause a buffer overflow on the affected device and allowing the attacker to execute arbitrary code on the device or cause an indefinite loop on the affected device which could then lead to a watchdog crash.
An Examination of 2017 Top 10 Vulnerabilities
Recently, Recorded Future released a list of the top 10 vulnerabilities used by cyber criminals in 2017. Microsoft and Adobe were the vendors whose products were affected the most. According to the report, the most exploited vulnerability in 2017 was the CVE-2017-0199 which allowed a malicious actor to download and execute Windows PowerShell commands whenever a user opens a document containing an embedded exploit. Documents that were used to exploit this vulnerability downloaded and executed malware payloads from several well-known malware families.
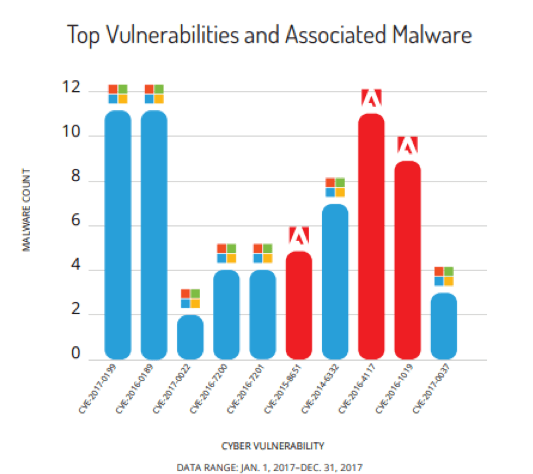
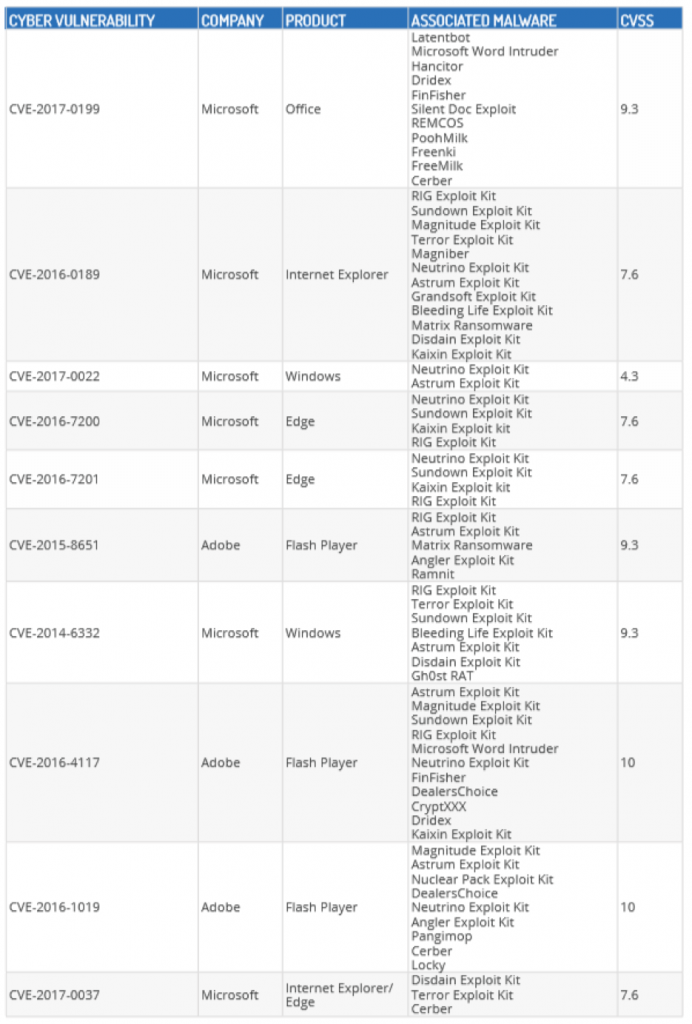
Image Source: Recorded Future
Table Source: Recorded Future
The CVE-2016-4117 which was the Adobe Flash Player Zero-Day Vulnerability was also a major vulnerability that was exploited by several cyber criminals in 2017. Attackers embedded this exploit inside a word document which was then hosted on a webserver, using a dynamic domain name system (DDNS) domain to reference the document and payload. This allowed attackers to disseminate their exploits via URL and email attachments.
What do attackers do once vulnerability has been discovered?
Once vulnerability has been discovered by a malicious actor, the next step in carrying out an unauthorised action is usually to carry out an exploit. An exploit is a piece of code written by malicious users to target a discovered vulnerability. Usually, this code is embedded within a piece of malware. Immediately the exploit written successfully executes, the malware then drops a copy of itself into the vulnerable system. On some occasions, instead of dropping an infected file, the exploited may be crafted in such a way that it drops another entirely different malware in the system. This can be a backdoor or a Trojan which can allow the malicious user then gain direct access and then steal critical information from the infected system.
How to stay protected from vulnerability exploits
In other to protect your computer system or organisational assets from exploiting the vulnerabilities listed above and other computer vulnerabilities, here are a few actions that should be taken:
- Prioritise the patching of all vulnerabilities including the ones identified above. Applying security patches provides protection against exploits that abuse system vulnerabilities.
- Remove all affected software from systems where they do not play key roles in the business processes. An example will be to remove all Adobe software from systems where they are actually not needed.
- CVE-2017-0037 which was the vulnerability in Microsoft Edge and CVE-2016-0189 vulnerability in Internet Explorer has CVSS scores of 7.6 each. Using the Google Chrome browser as your default browser is something that should be considered.
- A zero-day vulnerability refers to vulnerabilities that has just been discovered and is yet unknown to the software maker or to antivirus vendors. If zero-day attacks are carried out, users are advised to monitor the software vendors for security updates. Most of the time, a workaround solution is usually provided to address the exploitation of a flaw until an official patch is released.
- Systems hosting critical data and shared data are usually regular targets for ransomware attacks. Ensure these systems are properly backed up frequently.
Article written by Octavian Burghelea (SOC Manager at Smarttech247) and Joel Aleburu (Cyber Security Analyst at Smarttech247).
Contact Us
The data you supply here will not be added to any mailing list or given to any third party providers without further consent. View our Privacy Policy for more information.