Tuesday, April 10th, 2018
The Anatomy of a Compromised Network (Part 2)

In our last article, we began to examine the anatomy of a compromised network. We discussed what constitutes a compromised network and common ways by which network architectures get compromised. In this piece, we will be focusing mainly on how to identify a possible network compromise and discussing a few mitigation steps.
Just like the example in the previous post about the botnets and how certain smart systems from the experiment seemingly normal behaviours even after being infected, on some occasions a network compromise might occur without giving out any conspicuous signs. For example, if a well skilled attacker were to steal a piece information from a particular network over a very long period of time without getting caught, the attacker might want to attack the infrastructure as discreetly as possible and could make use of a covert channel. Most of the time, covert channels are not discovered until way after the attack has been successfully perpetuated. This is usually also the case with backdoors.
What then are the flags to look out for in order to recognise a compromised network infrastructure? Here are a few of them:
- Your Traffic is a Goldmine
Observing the traffic of the devices and endpoints in your network architecture can provide great information about a possible compromise of your network. As a rule of thumb, outbound traffic to IP addresses that are parts of blacklist sets or have low reputation is a strong indication of possible compromise. For example, if a device on your network is infected and has become a part of a botnet, the device will definitely attempt to connect to the command and control server to receive instructions and updates.
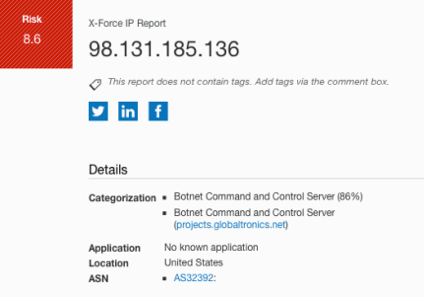
A lot can be observed from monitoring outbound traffic. If proper port filtering has been done with the firewall rules during the network design phase, we might want to be interested in traffic that originates from the endpoints outside the normally allowed ports. This is because when a device gets compromised, on many occasions, it attempts to communicate with a controlling server therefore, even if the traffic has been blocked. For example, if a device is seen attempting to make an outbound connection to an IP address such as 98.131.185.136 (which is a known Botnet server) via several ports, it might be an indication of a compromise. Like I have earlier pointed out, the reputation of the destination IP addresses can also provide a strong indication. Below is a summary of the reputation report of 98.131.185.136 gotten from IBM’s X-Force IP reporter.
Another common indication of a network compromise that can be observed from monitoring your network traffic is attempts to bypass or successfully bypassed established proxy servers. Usually, when a device on a network has been infected with a form of malware, it performs communication directly without going through any of the available established proxy servers. When proxy servers are in place, any traffic that originates from an endpoint and successfully establishes a session with an external host without going through the designated proxy server (unless otherwise configured) might be a very big red flag. This observation also applies to DNS queries originating from the network. Usually, devices on a network do not send DNS queries directly to the internet; it goes through a DNS server. Observing direct queries might as well be an indication that the setting on the DNS server has been hijacked.
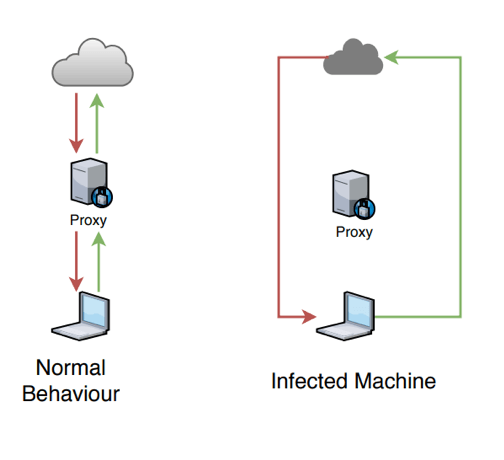
Figure 1: How Proxy Servers work vs Bypass
The scenarios presented above are only a few common observations that can be deduced from analysing network traffic. There are numerous other indicators of compromise that can be observed from analysing the entire traffic of your network. A huge spike in network traffic towards a particular application for example or excessive login attempts/brute forced logins etc.
- Lateral Movement and Interesting Tools
Lateral movement is a technique that malicious users use to progressively move through a network while searching for key target data and assets. It is basically the process of jumping from one machine to another to locate and access data with valuable information. This can be done using different connection types such as RDP, SMB, etc. or even using IT tools such as TeamViewer etc. If an insider or external attacker wanted to spy on confidential information on a system, a tool as simple as TeamViewer can come in very handy. Of course, ordinarily, that isn’t a form of malware so no antivirus will pick it up as a form of malware. Analysing system logins with these connections can be a pointer to a compromise of the network. For example, finding scripting tools or RDP sessions on a system that do not belong to the departments that use them and isn’t a known exception might be a strong pointer to a possible compromise. Installing these tools on an unsuspecting user’s computer can be done by attaching it to a carefully crafted phishing email.
Observing what tools are present and services are running on a computer and how much CPU power, computer memory and network bandwidth is being consumed can also go a long way in raising a red flag if a compromise has occurred.
- Suspicious Email Activity
If a device on your network has been infected and has become a part of botnet for example, that device might be used when sending spams. Some computer worms also find very interesting ways to replicate themselves and spread across a network by sending emails out to all contacts in the address book. Observing a sudden increase in email activity from specific computers on the network can be another strong indication of a compromise.
Apart from the three points explained in-depth above, some other indicators of a possible compromise include the following
- Observing suspicious activity on privileged accounts and new unauthorised privileged accounts.
- Suspicious logins or login attempts which might show signs of a brute force.
- Large amount of unexplained compressed files in very random and unexpected locations
- Change in registry configurations
- Very large amounts of request for a particular file
- Irregular geographical login locations
Overall, the need for network security monitoring over for a network infrastructure can never be over emphasised. Many of the scenarios listed above will be easily detected by having a proper network security monitoring framework in place. In this post, we have described how the SIEM works and how well detections are made. Not only will having constant monitoring provide information about what is going on in your network, it can also be used to spot certain anomalies that might be an indication of a network compromise. For example, a huge increase in activity HTTP (spike) from devices on a Sunday afternoon for a company that opens and works only on Monday to Friday might call for some further investigation.
What happens when it has been fully established that a network compromise has occurred? Check out our previous blog article we presented steps to fully recover from an established breach.
Contact Us
The data you supply here will not be added to any mailing list or given to any third party providers without further consent. View our Privacy Policy for more information.