Wednesday, March 28th, 2018
The Anatomy of a Compromised Network

A couple of years ago I had set up a honeypot to study the behaviour of botnets on smart systems. I was interested in how they become compromised and the speed at which different classes of remote commands are executed. One of the most interesting things that were observed was the seemingly normal behaviour several of the smart devices still continued to exhibit even after being a part of that botnet.
Network Compromise
Network compromise can occur in several ways. A network is compromised if there has been a breach in the confidentiality, integrity or availability of its infrastructure or components in any form. In this article we will discuss compromised network and how they can occur. Stay tuned on our blog for Part II where we will be giving a detailed analysis on how they can be recognised and mitigated.
One of the most basic functions of the (network) intrusion detection system is to detect any possible form of likely compromise on your network infrastructure and that’s because before an external malicious user can get access to a network infrastructure or an internal user can carry out any form of malicious action, there has to be some form of compromise. While compromises might exist in basic network design and implementation, for example leaving unnecessary ports open or doing unconventional things such as placing a domain controller in the DMZ. Before malicious actions can be carried out, the network first has to be compromised.
There are various ways in which a network can be compromised. An interesting one is the drive-by attack where malware with gets downloaded from insecure websites automatically and silently. Here are a few common ways in which a network infrastructure can be compromised:
Original Network Design Flaws:
Having a secure network infrastructure isn’t in anyway dependent on the number of security products applied on the network. While having security products will still go a long way in protecting your infrastructure, it still isn’t a substitute for having a properly constructed and secure design. The security of your infrastructure has to be exhibited from the network design phase. Network design flaws might simply create an expressway to network compromise. Just like the example we had provided earlier, placing the domain controller in a DMZ a typical example of a design flaw. Design flaws create holes that open your network to all manner of possible compromise. Some design flaws can go for years without being discovered until a major compromise occurs.
Social Engineering and Spear-Phishing:
Social engineering involves manipulating people to give up confidential information. On many occasions, this is used to give up username and password information. On many occasions, this is used when attempting to compromise a network in by sending phishing emails or even better, spear phishing. Phishing is an attempt by an unauthorised malicious user to gain confidential information by sending (usually) emails and getting the recipient to click a link or download an infected attachment. It gets even better and more complex at spear-phishing when the phishing attempt is properly constructed for a particular person or organisation to fall victim.
Malware Infections:
While analysing various kinds of malware, it is quite amazing how many libraries and functionalities are called by different types of malware and how hard they try to hide their presence on their hosts. In this category, worthy of mention are viruses, Trojans and worms.
Worms are self-replicating malware programs. They are also usually used as attack vectors for malicious users to exploit the network on a later date. Most worms are easily detected by good anti viruses depending on the complexity involved in its design however, some worms are designed in very complex manners that they are very difficult to detect by any antivirus (e.g Stuxnet). Worms have the ability to spread by themselves on the network. Just like any other attack vector, worms can enable malicious users exploit system vulnerabilities.
Trojan
A Trojan is a form of malware that presents itself like a helpful software application. The goal of a Trojan is to trick a user into granting it access to a computer system. Trojans usually need the user to click the install button by themselves. Many Trojans are also constructed to gain root access and provide backdoors to unauthorised users.
Unlike worms that self-replicate, viruses need human interaction to spread through the network. Viruses are malicious code that typically attaches itself to a file or executable program. The level of harm caused by a virus also depends on the kind of virus and the complexity in its design. Viruses can also be used to cause slight damages or wipe out systems completely.
Spyware can also be used to compromise a network. Spyware is used to gather information about a person or organisation without their knowledge. Apart from Viruses, Trojans, worms and spyware described above, on some occasions, malware might be customised in such a way that their signatures will not be detected by security measures put in place.
Waterholing:
A Waterholing attack can be used in compromising a network infrastructure. In Waterholing attack, an attacker compromises a website that is frequently visited by a user on the targeted network. When infected, the user’s computer then becomes connected to a command and control server. It then obtains instructions from an attacker. Waterholing attacks are usually very difficult to detect. Critical information present on a system can be leaked or lost through this method.
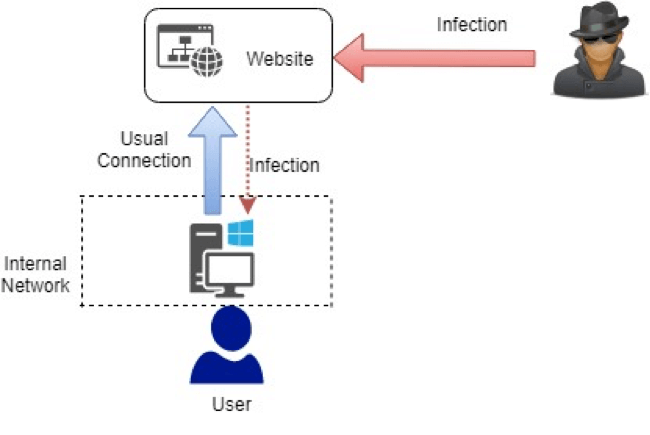
Figure 1: Waterholing Attack
Zero Day Exploits:
These attacks occur when a malicious user exploits critical vulnerabilities present in an operating system or application present which have not been generally known previously. They are quite interesting since they can go undetected for a very long period of time. As much as months or even years in some cases. Zero-Days can be used to carry out really huge attacks such as entire infrastructure takeovers or data theft. On many of the occasions, zero-day vulnerabilities are usually as a result of insecure software development practices.
There are several other ways in which an attacker can infiltrate a computer network hereby leading to a compromise. In the next piece, we will be taking a look at common ways to detect a compromised network and how the effecting consequences can be mitigated.
Contact Us
The data you supply here will not be added to any mailing list or given to any third party providers without further consent. View our Privacy Policy for more information.